Cloudflare Security Tips for Web3 Products
If you're using Cloudflare for your web3 product, it's important to rotate the Global API Key for all your accounts and remove all accounts added to your Cloudflare. Global API Keys are deadly and can rekt you even after you've rotated tokens, changed passwords, or revoked employee access in your offboarding. Learn more about Cloudflare security tips to protect your product.

Tay 💖
dont believe their lies
-
🚨 If you're using Cloudflare for your web3 product, stop what you're doing right now.
— Tay 🦊 💖 (@tayvano_) March 23, 2023
You NEED to:
1. Rotate the Global API Key for all your accounts
2. Remove all accounts added to your Cloudflare unless you rotated their Global API Key in step 1https://t.co/z913LMCc85 -
I know this sounds dramatic, but it's really not. Please do this. 🙏
— Tay 🦊 💖 (@tayvano_) March 23, 2023
The Global API Keys are deadly.
They will rekt you even after youve rotated tokens, changed passwords, or revoked employee access in your offboarding.
They will rekt you even if youre sure they cant rekt you pic.twitter.com/mzM61IKUCL -
These are not API tokens or access tokens. They don't have the perms you think they have.
— Tay 🦊 💖 (@tayvano_) March 23, 2023
Here's how you rotate the global key:
1. Go to your Cloudflare dashboard
2. My Profile > API Tokens
3. Go to the API Keys section
4. Find your key
5. "Change"https://t.co/z913LMCc85 -
But you can't rotate the Global API Key for accounts added to your CF.
— Tay 🦊 💖 (@tayvano_) March 23, 2023
Therefore, you need to remove those accounts.
1. Go to your Cloudflare dashboard
2. Manage Account > Members
3. Expand that member
4. Click Revoke > Yes, revoke accesshttps://t.co/GzXnaVeuRZ -
You should honestly remove/revoke/rotate any and all:
— Tay 🦊 💖 (@tayvano_) March 23, 2023
users
members
tokens
access keys
api keys
etc etc etc
that aren't ACTIVELY being used.
If it doesn't NEED to be there, kill it.
These are doors. They can, have, and will be used to exploit your product + users. pic.twitter.com/HkyvI8QX09 -
If you think you're are fine, you looked, blah blah. No, fuck you. Change them. Remove them. NOW.
— Tay 🦊 💖 (@tayvano_) March 23, 2023
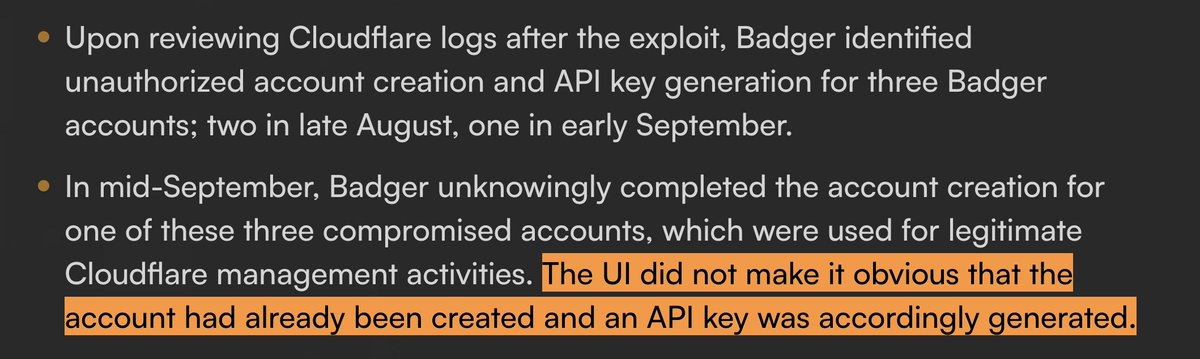
This has already rekt Moonpay/IOTA, BadgerDAO, KyberSwap, MyAlgo & more.
The permissions are NOT what you think they are.
And the activity will NOT show in your logs. pic.twitter.com/b7hLkP56kb -
The attacker created the key used to rekt these products MONTHS prior.
— Tay 🦊 💖 (@tayvano_) March 23, 2023
BadgerDAO = 3+ months prior
Moonpay/IOTA Trinity = 7+ months prior
KyberSwap = 11+ months prior
MyAlgo = 18+ months prior ‼️ ‼️ ‼️https://t.co/gNknCJRvFt pic.twitter.com/9wqufzMGDW -
This attacker is NOT to be underestimated.
— Tay 🦊 💖 (@tayvano_) March 23, 2023
They are patient beyond belief.
They evade detection.
They obfuscate.https://t.co/oCYDoI6xoj pic.twitter.com/RBGcyywjYG -
They wait.
— Tay 🦊 💖 (@tayvano_) March 23, 2023
They test their code.
They cover their tracks.https://t.co/iCSU1GpNdn pic.twitter.com/LQG9efCuei -
They push the malicious code on and off for short bursts of time.
— Tay 🦊 💖 (@tayvano_) March 23, 2023
They target certain wallets and avoid others.
The test and iterate the code. pic.twitter.com/ni8xbANUbB -
They will do this to you if you don't lock your shit down.
— Tay 🦊 💖 (@tayvano_) March 23, 2023
It's been over 3 years since the first incident. Its happened again and again and again.
No one is going to stop them from draining your users except *you*.
Please rotate your Cloudflare keys. Please. 🙏 pic.twitter.com/8IaRaVCC3o -
More recommendations on what to do / what to look for:https://t.co/rXsCDbUsv2
— Tay 🦊 💖 (@tayvano_) March 23, 2023 -
It should also be noted that these keys are technically "legacy" so if your product gets hacked and you contact Cloudflare, they will not be helpful here.
— Tay 🦊 💖 (@tayvano_) March 23, 2023
They will tell you to do a lot of things but it won't be anything around these keys, and it won't lock out your hacker. 😬
